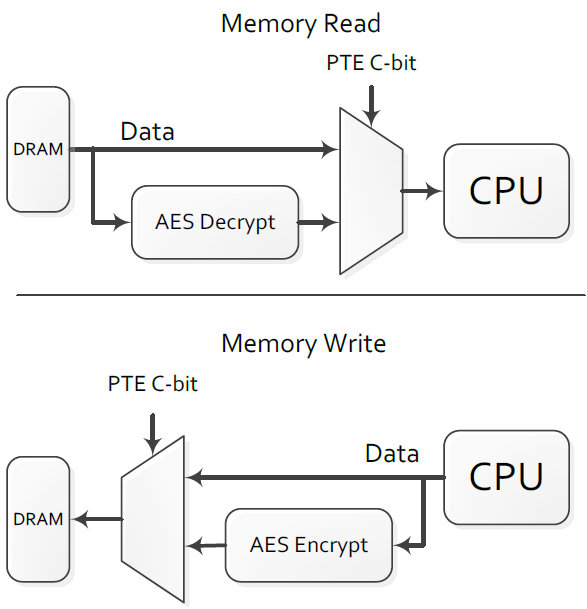
Is encryption in RTI Connext DDS Secure hardware-accelerated? | Data Distribution Service (DDS) Community RTI Connext Users

Efficient Android‐based storage encryption using multi‐core CPUs - Alomari - 2016 - Security and Communication Networks - Wiley Online Library



![What Is AES Encryption? [The Definitive Q&A Guide] What Is AES Encryption? [The Definitive Q&A Guide]](https://www.trentonsystems.com/hs-fs/hubfs/2-1.png?width=1920&name=2-1.png)